Simply log on to Friendster under your existing account, click on the link that says "My Settings" on the top right hand corner of the screen.
The next screen you're brought to will have an option that says "Cancel Account" so go ahead and click that and you'll have another confirmation screen after that.
Do remember that deleting your account is permanent and there's no way you can get any of it back!
Tuesday, December 25, 2007
How to Delete Your Friendster Account
at
5:04 PM
![]() .....
lAN
.....
lAN
Sunday, November 18, 2007
Remove Fake Windows Security Alert (Spyware)
Its a very annoying spyware, and maybe some antispyware cannot remove it. Try SmitfraudFix.
It will do the job.
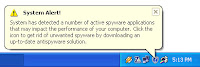
Download here
at
2:20 PM
![]() .....
lAN
.....
lAN
Tuesday, November 13, 2007
Best Technology Bling
Its name is Key. IronKey.
And it's the world's most secure flash drive. Designed so you can safely browse the Web and transport data, this James Bond-worthy flash drive also protects against phishing and pharming attacks, ID theft and keystroke loggers. Forgot your password? You've got 10 consecutive tries before—yup, you guessed it—the device (internally) self-destructs, wiping everything on its drive clean as a whistle. $79-$149. If more glam is what you seek, check out Swarovski's crystal-encrusted USB Memory Key. $178.
at
11:09 AM
![]() .....
lAN
.....
lAN
Thursday, November 08, 2007
Flash.10.exe remover
ues these remover to clean your infected PC. Its also fix all the registry error causes by the virus.
It also remove other variant of Flash.10.exe
Download here
at
11:59 AM
![]() .....
lAN
.....
lAN
Saturday, October 20, 2007
Yahoo! Connection Problems
Yahoo! on a Router, Firewall or Proxy!
People using Routers, Firewalls and Proxies often experience Yahoo! Messenger connection problems. The official Yahoo! support lacks detailed information, and misses some important facts! The following aims to break the information down, and explain easily in sufficient detail.
Connection Options
There are 4 connection Options.
These may be found from the Messenger menu, choose Perferences, and click Connection.
| Connection | When to use | |
| No Proxies | This is the default option for those who dont have any security issues, such as firewalls or connection through proxies. | |
| Firewall, No Proxies | This option is selected if a firewall is detected. This method forbids voice chat, super webcam, and p2p IM. This option is not recommended, unless you have no control over your firewall. | |
| Use Proxies | Use this when you have to connect through a proxy, HTTP (basic and slow) or SOCKS4 or SOCKS5(with authentication). Common in the workplace, or advanced security. | |
| No Network Detection | Recommended for everyone who doesn't require a proxy server, and has firewall control. The firewall option doesn't care that you open ports, it automatically blocks, this option does not perform any detection of your network type. |
Ports Yahoo! Messenger uses!
Yahoo! Messenger services uses a variety of ports.
| Service | Ports |
| Chat & Messenger | TCP Port 5050: Client Access only |
| Insider/Room Lists | TCP Port 80: Client Access only |
| File Transfer | TCP Port 80: Server Access. Your ISP may block this port, as its used for web hosting. You can change port in Messenger, Preferences, File Transfer. |
| Voice Chat | UDP 5000-5010 TCP 5000-5001: Client Access If UDP Fails, TCP will be used instead, see below. |
| WebCam | TCP Port 5100: Client Access |
| Super Webcam | TCP Port 5100: Server Access |
| P2P Instant Messages | TCP Port 5101: Server Access PMs between Buddys may not use the Yahoo! Server, but this is not a requirement. |
TCP versus UDP
TCP is a reliable protocol, and all data sent has a number of extra fields that guarantee delivery. This creates large overhead, and can make the stream slower.
UDP does not carry the same overhead, the data is transmitted much faster, but some data may not be delivered.
If you use a firewall
You need to enable the application Yahoo! Messenger, filename ypager.exe to access the internet, in most personal firewalls, this will give Yahoo! Messenger access to anything it desires, in client mode.
For server mode, you will most likely be prompted.
Proxy Users
HTTP Proxy is slow and unreliable, you cannot access voice chat, or webcam, or any of the advanced interactive services.
SOCKS4 and SOCKS5 are common in the workplace, as they allow more ports to be closed. SOCKS5 requires authentication available from your administrator.
Routers
If you use a router, client access to the Yahoo! Services will be as simple as if you did not use a router.
Where server access is required, you will need to use port forwarding or port triggering.
Port Forwarding/Virtual Server/Forwarding
You need to tell your router which computer on your network to forward the server packets too. This usually follows the form of specifying the computers IP, such as 192.168.1.2, the start port, and end port (from the table above, such as start 80 end 80 for file transfer, 5100 and 5100 for super webcam), and a map port (the same as the start and end).
WebHazard has a graphical tutoral on how for the D-Link routers for Yahoo! Voice Chat. View that here.
Port Triggering (LinkSys) - Super Webcam/UDP Voice
LinkSys routers allow a dynamic form of port forwarding, called port triggering. They maintain a connection tracking, when messenger makes a specific connection, the router is notified that an incoming server connection may follow
For UDP voice, a packet outgoing on port 5000 may cause a response to arrive on another port, say 5001. Linksys routers may be told to expect this, by setting the triggering range to 5000-5010, and the incoming range to 5000-5010.
For webcam, a packet outgoing on port 5100 will tell the router a server connection may come in on port 5100, setting the same ranges.
at
7:44 PM
![]() .....
lAN
.....
lAN
Labels: internet, Yahoo Messenger
Saturday, October 13, 2007
Linux Transformation v1.1

The Power DeskMod Linux Transformation had an installation in the format RAR, more easy!
In pack it comes:
Tema of the Ubuntu and Debian
Icones and cursors for IconPackager
Fontes _Wallpapers
Yod'm 3D (desktop in cube)
Download
at
10:00 PM
![]() .....
lAN
.....
lAN
Labels: Operating System, tips and tricks
Sunday, October 07, 2007
Default router password
Default router password here
at
5:27 PM
![]() .....
lAN
.....
lAN
Labels: security, tips and tricks
very funny -Theres no place like 127.0.0.1
funny .. very funny ... never thinked like this before. That's must be cool to trick non techie people especially the script kiddies :lol:
chatlog 1
#60852
Numi: hey, can you guys just check a site out and tell me if it's up?
Haddock: depends, what is it?
Numi: just my apache server, it works for me but seems to be down for anyone else
Haddock:alright, what's the address?
Numi: http://127.0.0.1
Haddock: ......
Haddock: ...Yeah, it's up.
chatlog 2
#38640
darthv: ok
*** darthv has quit IRC (Ping timeout)
chatlog 3
HaX.1337: U're all lame as hell here!!!!! I can hack u all in no time! just tell me your ip and u're dead!
Maler.home: try mine
Maler.home: 127.0.0.1
*** Signoff: HaX.1337 (Connection reset by peer)
Damz|dispute: wow. never thought such a retard nick can get his hands on something actually working xD
* bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
bitchchecker: why do you kick me
bitchchecker: can't you discus normally
bitchchecker: answer!
Elch: we didn't kick you
Elch: you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker: what ping man
bitchchecker: the timing of my pc is right
bitchchecker: i even have dst
bitchchecker: you banned me
bitchchecker: amit it you son of a bitch
HopperHunter|afk: LOL
HopperHunter|afk: shit you're stupid, DST^^
bitchchecker: shut your mouth WE HAVE DST!
bitchchecker: for two weaks already
bitchchecker: when you start your pc there is a message from windows that DST is applied.
Elch: You're a real computer expert
bitchchecker: shut up i hack you
Elch: ok, i'm quiet, hope you don't show us how good a hacker you are ^^
bitchchecker: tell me your network number man then you're dead
Elch: Eh, it's 129.0.0.1
Elch: or maybe 127.0.0.1
Elch: yes exactly that's it: 127.0.0.1 I'm waiting for you great attack
bitchchecker: in five minutes your hard drive is deleted
Elch: Now I'm frightened
bitchchecker: shut up you'll be gone
bitchchecker: i have a program where i enter your ip and you're dead
bitchchecker: say goodbye
Elch: to whom?
bitchchecker: to you man
bitchchecker: buy buy
Elch: I'm shivering thinking about such great Hack0rs like you
* bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
Thursday, September 13, 2007
A compact utility for several google hacks

Turn Google into an even more powerful search engine with the recent update to the previously mentioned Google Hacks. The updated version of Google Hacks can now search lyrics, fonts, applications, torrents, cache, web hosting, and use Google as a proxy.Google Hacks is becoming quite a nifty app. Google Hacks is a free download for Windows, Mac, and Linux
::Google Hacks::
Hacks is meant as this definition. "A Hack is a modification of a program or device to give the user access to features otherwise were unavailable to them. " Wikipedia.
at
9:37 PM
![]() .....
lAN
.....
lAN
Meebo now supports file transfer!!
Popular web-based instant messaging service Meebo now supports file transfer, meaning you can share files with your contacts over Meebo IM on the web—whether your contacts are using Meebo or not. You'll need to have registered with Meebo (a free and painless process) in order to send files from their web interface, but anyone can receive files.just click
on this icon
at
8:55 PM
![]() .....
lAN
.....
lAN
Labels: Computing, internet, tips and tricks, Yahoo Messenger
Tuesday, September 11, 2007
Speed Up Your Work in Photoshop
Any project that you work on in Photoshop will have some repetition. Certain projects (like creating seamless pattern tiles) will have a lot of repetion. By following the next two steps, you should be able to speed up your work considerably.
First, learn some common keystrokes. It will only take a few minutes, and I promise you won't regret it.
Here are the keystrokes that I use most often. Mac users, substitute the Command key for the Control key:
Ctrl+A Select all
Ctrl+C Copy
Ctrl+V Paste
Ctrl+S Save
Ctrl+D Deselect
Ctrl+Z Undo
Ctrl+U Adjust Hue/Saturation
Ctrl+X Cut (useful for layers)
at
8:22 AM
![]() .....
lAN
.....
lAN
Sunday, September 09, 2007
How To Remove haha.js
Its a javascript and not that really harmful to your PC but a little bit annoying though. Most noticeable effect if your PC are infected with this worm is the tittle bar of your IE change to "haha" word.
Some of the antivirus does detect this worm. Here is the way how to remove it manually..
Step 1
On your mycomputer menu option go to Tools>Folder option
uncheck box "hide protected operating system files"in Tool-Folder options and check "show hidden files".
Step 2
Open Task Manager by pressing ctrl+alt+del. End Process all Wscript.exe that you can found in the Task Manager(some times it can be more than one process)
Step 3
Open mycomputer and search for haha.js files and delete it there should be an autorun.inf file comes with this haha.js just delete it
*this haha.js run when you use double click to open your drive c: ,d: ,e: ..when removing this worm use right click instead to open any drives. Don't forget to look and delete this haha.js in your external hd and thumbdrive
Step 4
Go to Run type msconfig. At the startup tab look for any haha.js @ wscript.exe unchecked and delete the key location in the registry.
finally restart your PC. Good luck on trying!
at
12:08 PM
![]() .....
lAN
.....
lAN
Labels: Computing, security, tips and tricks
Should you turn off your PC
Should you turn off the computer or the monitor when it is not in use?
Alternatively, should it be left in Standby mode?
When you turn on electrical equipment it uses a large amount of power, and then it goes down to its “rated consumption” as stated on the label. This is measured in watts or kilowatts. This sudden jump in electricity is know as a spike. You can see it on a digital power meter, but there is a way that it can be observed more easily.
Just switch on your air conditioner, refrigerator, or vacuum cleaner. It’s best if that appliance is plugged into the same circuit for the purpose of this experiment.
Your lights may dim briefly and then resume their former brightness during this “spiking” and it will then go back to its normal level of power.
Another way of looking at this is with a standard incandescent light bulbs. Have you noticed that they seem to be able to stay on forever, but they burn out when you turn them on? That’s also because of that initial spike of electricity.
So, what’s the problem?
Computers have delicate electronics inside of them. The electronics in laptops may be even more delicate. As the computer ages, the components suffer from repeatedly being turned on and off (technicians say that the parts are fried). Over the course of time, the repeated spiking damages some components. It is thus a good idea to reduce the number of times that you spike these delicate parts.
So, computers should be left on, right?
Well, laptops heat up more than desktop computers, so it is not a good idea to leave them on. Laptops do not have the same system of fans that is in desktop computers. Leaving it on will fry the parts in a different way than turning it off and on, but the result will be effectively the same.
OK, so I’ll leave the computer in Standby or Hibernate mode
Those modes are different, as follows:
Standby
- The machine is powered down so that it uses practically no power.
- Your data is saved (if you have enough installed memory)
Hibernate
- The machine is powered off.
- The data is saved as an “image” on the hard drive. When you turn on the computer, everything is where it was. Unsaved unsaved work is restored, Windows is in its familiar position, and you can continue working.
Lower your electric bill
Hibernation and standby options are available because laptops have limited battery life and desktop computers use a considerable amount of electricity.
The “Energy Star” power consumption rating shows that manufacturers are becoming aware of the environment.
Standby mode is useful when a laptop is moved from one location to another. Batteries last significantly longer between recharges.
Hibernate, on the other hand, is not as useful. It takes nearly as long to power up to your previous state, and you still spike the mainboard during this time. You may want to use it because your Desktop seems to appear the same as the last time it was used.
Standby mode therefore seems to be a better option for extending the life of laptop. This is important, because laptops cost more and they are replaced less frequently. This issue is less important with a desktop computer.
There is still another option: You can have many of the benefits of switching the computer off and having the benefits of Standby mode.
Use the power setting in the Control Panel
Many computer programs “leak” memory. If a computer program uses 15MB when it is started, it may use 55MB two weeks later. This has nothing to do with anything you’ve done, and it is not because the program is working any harder. The programs leak memory because they are written and designed poorly.
What is the solution?
Restart your computer periodically. Better yet - leave it off overnight from time to time so that the parts can cool down to room temperature. I turn off my own computer once a week for Shabbat. I find that to be a reasonable compromise.
During the week, between these rest breaks, use the standby function in order to prolong the lifetime of your investment.
at
12:07 PM
![]() .....
lAN
.....
lAN
Labels: Computing, tips and tricks
Thursday, September 06, 2007
CBT nugget Certified Ethical_Hacker

CBT Nugget Certified Ethical Hacker Series
This video tutorial is good for someone who intend to be Certified Ethical Hacker. A good tutorial and direct explanation of hacking series. There is also a demo of hacking itself but its a very basic one. Its good expose for a newbie
http://rapidshare.com/files/26928682/Specialized_Solutions_Certified_Ethical_Hacker_Disk1.part1.rar
http://rapidshare.com/files/26928873/Specialized_Solutions_Certified_Ethical_Hacker_Disk1.part2.rar
http://rapidshare.com/files/26929190/Specialized_Solutions_Certified_Ethical_Hacker_Disk2.part1.rar
http://rapidshare.com/files/26929448/Specialized_Solutions_Certified_Ethical_Hacker_Disk2.part2.rar
http://rapidshare.com/files/26929585/Specialized_Solutions_Certified_Ethical_Hacker_Disk3.part01.rar
http://rapidshare.com/files/26929729/Specialized_Solutions_Certified_Ethical_Hacker_Disk3.part02.rar
http://rapidshare.com/files/26930079/Specialized_Solutions_Certified_Ethical_Hacker_Disk3.part03.rar
http://rapidshare.com/files/26930346/Specialized_Solutions_Certified_Ethical_Hacker_Disk4.part1.rar
http://rapidshare.com/files/26932809/Specialized_Solutions_Certified_Ethical_Hacker_Disk4.part2.rar
http://rapidshare.com/files/26932983/Specialized_Solutions_Certified_Ethical_Hacker_Disk5.part1.rar
http://rapidshare.com/files/26933070/Specialized_Solutions_Certified_Ethical_Hacker_Disk5.part2.rar
http://rapidshare.com/files/26933226/Specialized_Solutions_Certified_Ethical_Hacker_Disk6.part1.rar
http://rapidshare.com/files/26933293/Specialized_Solutions_Certified_Ethical_Hacker_Disk6.part2.rar
http://rapidshare.com/files/26933666/Specialized_Solutions_Certified_Ethical_Hacker_Disk7.part1.rar
http://rapidshare.com/files/26934711/Specialized_Solutions_Certified_Ethical_Hacker_Disk7.part2.rar
http://rapidshare.com/files/26934942/Specialized_Solutions_Certified_Ethical_Hacker_Disk8.part1.rar
http://rapidshare.com/files/26935055/Specialized_Solutions_Certified_Ethical_Hacker_Disk8.part2.rar
http://rapidshare.com/files/26935498/Specialized_Solutions_Certified_Ethical_Hacker_Disk9.part1.rar
http://rapidshare.com/files/26935673/Specialized_Solutions_Certified_Ethical_Hacker_Disk9.part2.rar
Saturday, August 11, 2007
Disk Cleanup Freeze?
It's a very common problem that many newbies almost always ignore to correct; that when you try to the Disk Cleanup tool, it may stop responding and you may receive the following message:
Disk Cleanup is calculating how much space you will be able to free on (C:).
This may take a few minutes to complete.
Scanning: Compress old files
This problem happens when there is an incorrect entry in the registry that is used by the Disk Cleanup utility to locate compressed files. In my view, I've noticed it happening to clean formatted computers as well, so I would suppose that the problem in the registry too is probably a faulty of M$ programming.
But here is a good little trick to follow if this happens to you:
1. Create a registry file by "right clicking" on the desktop > New > Text Document.
2. Name it anything you want with .reg extension. For example: diskcleanup.reg
3. Right click this file > Edit.
4. Type in the following code, then save and close:
Windows Registry Editor Version 5.00
[-HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\VolumeCaches\Compress old files]
That's it! It should have done it. Try running the Disk Cleanup now and see if it is any faster than before.
This tutorial has been test to work on WinXP Pro and Home only. That doesn't mean it won't work in other WinOS. Just that it's not been tested in others.
at
11:49 AM
![]() .....
lAN
.....
lAN
Disable Error Reporting
Whenever either Windows crashes, you will be asked if you want to send an error report to Microsoft. It's annoying, so here's a way to disable it:
1. Open the Control Panel.
2. Click on System.
3. Click on the Advanced tab.
4. Click on ERROR REPORTING at the bottom.
5. Select DISABLE ERROR REPORTING.
6. Click OK.
It's as easy as that.
at
11:46 AM
![]() .....
lAN
.....
lAN
Labels: Computing, Operating System, security
Guidelines to prevent computer-related stress injuries
Many guidelines have been published about computer-related stress injuries. This page summarizes some of my favorite suggestions.
- Stretch while seated at your desk in order to prevent some injuries.
- The target field (the size and point on the screen that you look at) should be set so that it can be seen conveniently without shifting or tilting your your head. You should be able to see the top of the target field. An adjustable monitor stand may help. Your head should face in a straight, neutral position - not facing either upward or downward.
- Exercise while at your desk. Drop your head gently forward. Slowly rotate it clockwise and counterclockwise. Blink frequently to moisten your eyes so that they feel less tired. You may need to use use eye drops to moisten them still more if you stare at the screen too long.
- Stare at a distant object from time to time. You may want to look out the window at a fixed object and then look at something else nearby, like your phone. Keep shifting your point of vision.
- Adjust your chair so that your neck is always straight while facing the screen. Don't hold the phone between your neck and shoulder. If you use the phone a great deal, buy a telephone headset.
- Use your right hand to hold on to the seat of your chair. Move your head forward, and then turn and lean to your left. You will feel a stretch from the neck to the top of the shoulder blade. Keep stretching for fifteen seconds. Reverse - do it with your left hand and lean to the right.
- If you feel that your shoulders are beginning to be rounded after an extended period of time in the same position, correct it by sitting up with a straight back.
- Slowly move your shoulders up and down. Let your arms hang down next to you, and then rotate your shoulders clockwise and counter-clockwise.
- Adjust the height of your keyboard and chair so that your arms and elbows are close to your body, and so that your elbow is at a right angle.
- Raise your right arm as if to throw an object. Keep stretching back a bit further. Gradually straighten your arm at the elbow. Your arm will then be behind and next to you. Slowly turn your palm upward. Gradually extend your fingers until you feel your muscles stretching at your forearm and wrist. Do it again, this time with your left arm.
- Straighten your back. Your arms should be next to you with your elbows bent at a 90-degree angle. Make fists with both hands. Rotate your elbows forward, but keep your fists in front of your waist. Straighten your elbows. Stretch your arms back behind your body. You'll feel your forearm and wrist muscles stretching.
- Your wrists should remain straight as you type. Adjust your keyboard shelf or seat so that they do not go up or down. You may want to put down your keyboard's little folding "feet". You may want to consider a foam wrist pad for support if your arms get tired from too much typing.
- Look for a comfortable mouse. There are special mouses (yes, that's the plural form for a computer mouse) for lefties and righties, and for small or large hands.
- Hold both hands in a clapping position. Use the palm of one hand to press back the wrist and fingers of the other hand. After three seconds, rest and then repeat this stretch for your other hand. Do this procedure five times for each hand.
- Keep your fingernails short, so that you don't have to use the pads of your fingers. Your fingers should be relaxed and slightly curved when typing.
- While keeping your wrists straight, stretch the fingers of both hands apart as widely as you can for three seconds. Relax. Do it again and again, for a total of five times.
- Sit straight. Keep your supplies handy so that you don't have to stretch for them.
- This exercise and the following one may be dangerous for those who suffer from back problems: Touch your shoulders with your fingertips while sitting at the edge of your chair. Gradually twist and stretch right to left.
- Lock the fingers of your hands together behind your head. Slowly tilt and stretch your body from side to side.
- Your lap and your feet should rest comfortably. They should be parallel to the floor. Either adjust your seat or use a footrest with a nonslip surface. Be sure there is enough room under your desk to stretch your legs.
- Take frequent but short walks. Handle small errands in the office yourself, as an excuse to get up and walk around. It's best to get up every twenty to thirty minutes, and you should never sit in the same position for more than 2 hours. From time to time, take a fast-paced walk around the neighborhood. Unless your neighborhood is even more dangerous than the effects of repetitive stress injuries.
Should you turn Off your PC?
Should you turn off the computer or the monitor when it is not in use?
Alternatively, should it be left in Standby mode?
When you turn on electrical equipment it uses a large amount of power, and then it goes down to its "rated consumption" as stated on the label. This is measured in watts or kilowatts. This sudden jump in electricity is know as a spike. You can see it on a digital power meter, but there is a way that it can be observed more easily.
Just switch on your air conditioner, refrigerator, or vacuum cleaner. It's best if that appliance is plugged into the same circuit for the purpose of this experiment.
Your lights may dim briefly and then resume their former brightness during this "spiking" and it will then go back to its normal level of power.
Another way of looking at this is with a standard incandescent light bulbs. Have you noticed that they seem to be able to stay on forever, but they burn out when you turn them on? That's also because of that initial spike of electricity.
So, what's the problem?
Computers have delicate electronics inside of them. The electronics in laptops may be even more delicate. As the computer ages, the components suffer from repeatedly being turned on and off (technicians say that the parts are fried). Over the course of time, the repeated spiking damages some components. It is thus a good idea to reduce the number of times that you spike these delicate parts.
So, computers should be left on, right?
Well, laptops heat up more than desktop computers, so it is not a good idea to leave them on. Laptops do not have the same system of fans that is in desktop computers. Leaving it on will fry the parts in a different way than turning it off and on, but the result will be effectively the same.
OK, so I'll leave the computer in Standby or Hibernate mode
Those modes are different, as follows:
Standby
- The machine is powered down so that it uses practically no power.
- Your data is saved (if you have enough installed memory)
Hibernate
- The machine is powered off.
- The data is saved as an "image" on the hard drive. When you turn on the computer, everything is where it was. Unsaved unsaved work is restored, Windows is in its familiar position, and you can continue working.
Lower your electric bill
Hibernation and standby options are available because laptops have limited battery life and desktop computers use a considerable amount of electricity.
The "Energy Star" power consumption rating shows that manufacturers are becoming aware of the environment.
Standby mode is useful when a laptop is moved from one location to another. Batteries last significantly longer between recharges.
Hibernate, on the other hand, is not as useful. It takes nearly as long to power up to your previous state, and you still spike the mainboard during this time. You may want to use it because your Desktop seems to appear the same as the last time it was used.
Standby mode therefore seems to be a better option for extending the life of laptop. This is important, because laptops cost more and they are replaced less frequently. This issue is less important with a desktop computer.
There is still another option: You can have many of the benefits of switching the computer off and having the benefits of Standby mode.
Use the power setting in the Control Panel
Many computer programs "leak" memory. If a computer program uses 15MB when it is started, it may use 55MB two weeks later. This has nothing to do with anything you've done, and it is not because the program is working any harder. The programs leak memory because they are written and designed poorly.
What is the solution?
Restart your computer periodically. Better yet - leave it off overnight from time to time so that the parts can cool down to room temperature. I turn off my own computer once a week for Shabbat. I find that to be a reasonable compromise.
During the week, between these rest breaks, use the standby function in order to prolong the lifetime of your investment.Friday, August 10, 2007
Yahoo!!
 If you go to Yahoo! Messenger official download page to download latest version of Yahoo! Messenger (8.1.0.413), you will end up with a small installer file which will in turn need to be installed and run to download the full setup files for Y! Msgr, and then only complete the installation of Y!Mgr. It’s not a good idea if you prefer to perform offline installation, and troublesome for those without want to install Yahoo! Messenger on PCs without Internet access.
If you go to Yahoo! Messenger official download page to download latest version of Yahoo! Messenger (8.1.0.413), you will end up with a small installer file which will in turn need to be installed and run to download the full setup files for Y! Msgr, and then only complete the installation of Y!Mgr. It’s not a good idea if you prefer to perform offline installation, and troublesome for those without want to install Yahoo! Messenger on PCs without Internet access.
However, as with previous version of Yahoo! Messenger, it’s possible to download full complete standalone installer setup file for Yahoo! Messenger via a direct download link. This stand alone setup program can install Yahoo! Messenger offline, and will install straight away without downloading anything extra. It’s the same file that the small Yahoo! Messenger setup initiator downloads if you download the ‘partial installer’ from Yahoo!.
at
3:24 PM
![]() .....
lAN
.....
lAN
Labels: Computing, internet, Yahoo Messenger
10 rules of internet safety
Nobody can ensure you that your network and computer is 100% safe even though you have installed the most advanced and updated firewall, antivirus software or even with the assistance of some hardware/electronic gadgets. As a user, you need to have some fundamental knowledge to minimize the risk of your private information being stolen and to make sure that your networking system is safe to use.
If you are not an IT technical personnel, perhaps the following 10 rules can assist you: -
- Do not use simple information such as your son’s name, your birthday, etc for your password. Use more complicated passwords. You can use the combination of small and big capital letter; add in special character such as $, %, &, etc.
- Do not simply click on any links that appears on the email received. Don’t reveal your private and personal information to any company if required via email.
- Do not place confidential printouts on your working desk. Keep them properly as the information might reveal some sensitive data. Lock your PC or set a password on the screen server if you leave your desk.
- Sometime you might receive some email from friends or relatives requesting you to forward some information. Be careful as this email might be a trap and carries spam. To verify the information, you can go to websites such as www.snopes.com to check.
- Do not simply open any attachment provided you 100% know the sender and the attachment’s content.
- Make sure your antivirus software’s scanning machine is running all the time. Do not simply switch off your scanning machine.
- Do not simply install software even though it is free. A lot of software that is free for downloading from the internet always carries virus or spam.
- Seek help from your MIS people if you are having any difficulty.
at
3:18 PM
![]() .....
lAN
.....
lAN
Saturday, August 04, 2007
Wonder kid joining MU
LONDON, Aug 2 (Reuters) - Manchester United have signed a gifted nine-year-old after his grandfather sent the Premier League champions a DVD showcasing the boy's talents which has become a YouTube sensation.
Rhain Davis, who was born in England but has lived in Australia since the age of four, was hailed by the British press on Thursday as the next Wayne Rooney after the United striker.
ADVERTISEMENT
The boy's dribbling and goalscoring prowess for an Under-10 side in Brisbane, Australia, feature in a four-minute YouTube clip, already viewed more than 800,000 times.
United confirmed the signing but played down the hype around Davis, who has moved back to Cheshire in northern England with his father, near the club's training ground.
"He's a member of our academy and we don't comment on individual members," a United spokesman told Reuters.
He added that the club sign about 40 players of Davis's age every year and, as is standard, will decide annually whether to renew his contract or release him.
What was so unusual in Davis's case was that his skills were brought to the attention of United's youth scouts by the DVD submission, which could inspire other hopefuls, the spokesman said.
"We're bracing ourselves for a whole series of DVDs," he added.
Davis has been thrilled at the chance to rub shoulders with some of his idols.
"The best part has been meeting lots of players like Wayne Rooney," he told British newspapers.
at
9:06 AM
![]() .....
lAN
.....
lAN
Monday, July 30, 2007
Monday, July 23, 2007
Google e-books
More google e-books get it or regret it.I'm also still reading it, and here i share it with you
Google Adsense Secrets
Google Secrets How To Get A top 10 Ranking
How to Hacker
modern Zen poem has it:
To follow the path:
look to the master, follow the master, walk with the master, see through the master, become the master.
read this how to hacker e-book
Sunday, July 22, 2007
BIOS Beep Code
What is a BIOS Beep Code?
When you power on a computer the BIOS immediately takes control of the computer and performs the P.O.S.T (Power On Self Test). At the end of the POST the computer will play an audible 'BEEP' through either the PC's internal speaker of through speakers attached to the sound card (if you have a built-in sound chip). If the POST completed successfully without detecting any problems with then system will play a single short beep to let you know the test is complete and the computer will continue to startup and load the operating system.
Below is a table of the most common AMI, Phoenix and Award BIOS beep codes.
AMI (American Megatrends International) BIOS Beep Codes.
AMI BIOS uses beeps of the same length and pitch. The error is displayed as a number of beeps. For example, 4 beeps indicated a timer failure.
| BEEP CODE | MEANING | POSSIBLE CAUSE |
| 1 Beep (No video) | Memory refresh failure | Bad memory |
| 2 Beeps | Memory parity error | Bad memory |
| 3 Beeps | Base 64K mem failure | Bad memory |
| 4 Beeps | Timer not operational | Bad motherboard |
| 5 Beeps | Processor error | Bad processor |
| 6 Beeps | 8042 Gate A20 failure | Bad CPU or Motherboard |
| 7 Beeps | Processor exception | Bad processor |
| 8 Beeps | Video memory error | Bad video card or memory |
| 9 Beeps | ROM checksum error | Bad BIOS |
| 10 Beeps | CMOS checksum error | Bad motherboard |
| 11 Beeps | Cache memory bad | Bad CPU or motherboard |
Award BIOS Beep Codes
Award BIOS uses beeps of varying duration. A long beep will typically last for 2 seconds while a short beep will last only 1 second. Award BIOS also uses beeps of different frequency to indicate critical errors. If an Award BIOS detects that the CPU is overheating it may play a high pitched repeating beep while the computer is running.
| BEEP CODE | MEANING | POSSIBLE CAUSE |
| 1 Long, 2 Short | Video adapter failure | Bad video adapter |
| Repeating (Endless loop) | Memory error | Bad memory or bad connection |
| 1 Long, 3 Short | Video adapter failure | Bad video adapter or memory |
| High freq. beeps (while running) | CPU is overheating | CPU fan failure |
| Repeating High, Low beeps | CPU failure | Bad processor |
Phoenix BIOS uses beep code patterns to indicate problems. In the table below the '-' indicates a brief pause between beeps.
|
at
12:15 PM
![]() .....
lAN
.....
lAN












