- Tell me about yourself.
- What are your greatest weaknesses?
- What do you worry about?
- Can you work under pressure?
- What was the toughest challenge you ever faced?
- What was the toughest decision you ever had to make?
- Why should I hire you?
- What do you for when you hire people?
- How do you feel about working nights and weekends?
- Where could you use some improvement?
Friday, June 29, 2007
10 Favorite Interview Question
at
6:46 PM
![]() .....
lAN
.....
lAN
Tuesday, June 26, 2007
Monday, June 25, 2007
What You Should Know About Cyber Security
A decade ago, people who setup and maintained servers, had very little knowledge of basic skills in security. Even today, average folks usually establish servers, websites and businesses, many of who have little security experience.
Ordinary users are pacified when big corporations make statements about how secure their servers/applications are. Nothing could be far from the truth. Each month we have more cases of hackers breaking into some server systems and stealing information.
But why should you care about all this? I could tell you greatly about all the websites defacements, stolen corporate secrets, or the break-ins to government servers, but let's give you a more personal reason to why should you care?
Let's ask you, the reader a question? Do you think your organization's data is valuable? How about all the contact lists, emails, credit card numbers that you have collected, or your current marketing strategies, financial reports, aren't these valuable.
What if I told you that I could break into any of these systems? What could I do? I could basically steal your credit card number and use it all over the country, destroying your bank account. I could change your records so you don't get any kind of service anymore.
I could access your confidential information to your competitor. I could get your phone disconnected. Or even worse, if you have an e-commerce site, I could crash it so you lose a lot of money.
Or what if I am working in your company as an employee and I'm not happy, I could launch a DOS (Denial of Service) attack so that no information can be accessed over network. I also with a few well-placed Trojans, can corrupt your entire database.
Are you convinced why we need security measures?
The problems with security can be grouped into four basic heading:
1. Network and Host Misconfigurations
2. Operating Systems and Applications Flaws
3. Irresponsible Vendor Effort or Response
4. Lack of Qualified People in the Field
Host Misconfigurations
This is responsible for most of the security breaches that take place. Many times even system administrators are not aware of the servers running on their servers. You may ask how is that possible? Think of some thing as simple as your word processor. How many of its services do you use or are aware off? Even some thing as simple as writing macros would put you in advance users category. Most people just use the basic functionalities save, spell, check, tables etc.
The same concept applies to the OS and software. The dynamic nature of the industry is such that a few can ever keep up with it. And such a machine when connected to the net is just waiting to be hacked.
Some basic examples of these types of utilities and services include:
1. Network Printing Utilities
2. Remote System Configuration Utilities
3. File Sharing Utilities
4. Sample CGI Programs and Scripts
These with default or misconfigured settings are the most common to being hacked especially if they have known vulnerabilities.
Application Flaws
Vulnerabilities due to flawed programming are other security breach and one, which is quite out of the control of the user. Vendor failure is the most common source of security problems. For instance, one of the most common used exploits is the IIS server and Microsoft. Other includes ISC's BIND (an implementation of the DNS), SSH (Secure Shell) or many services found in Sun's Solaris OS. One of the most common email program Outlook Express has constantly been a target of Trojans due to its programming nature. Remember the "I LOVE YOU" virus or "Melissa".
Irresponsible Vendors
Many vendors have no idea what is going into their codes. There is very little quality assurance in the software industry. We use substandard programmers to save money on development. Who would end up paying for the negligence of the vendors? The end users would by having their networks and computer breached.
Or even in the case of slow patch response, for example, issuing patches, would compromise security. Exploits travel at the speed of light in the hacker community. From email lists and discussion groups to IRC chats. They are alive with the latest exploits of one group or another. And if the vendor is slow in responding, there are many computers, which would be hacked virtually over night.
Incompetent Consultants
Even if all of the above problems would be resolved, companies would still find other problems on their hands such as the lack of qualified people. It's a hard job finding even a competent systems engineer, administrator or programmer, much less a security professional.
And you can't get training that can make you a security professional within days. It's a very long process, which takes into account TCP/IP, hardware, OS and basics of cryptography and programming. This would enable you to understand basics of security.
This lack of personnel contributes to misguided or absent information security programs within organizations. Policies are incomplete or non-existent. And this would leave your system vulnerable to attacks.
So how exactly do hackers break into systems?
Some people might want to prosecute me for distributing this information. Why? Simply because the information might be used to harm rather than for good. I'm not saying this information cannot let you do that. But only they can protect themselves, those who know what to look out for. All this information is available freely on the web and is known to all hackers. The ordinary user does not usually make an effort to acquaint them with it. That is more dangerous. This article would give them a brief insight to what they should expect.
Hacking is a nine part process as described in the book Hacking Exposed. It includes:
1. FootPrinting
2. Scanning
3. Enumeration
4. Gaining Access
5. Escalating Privileges
6. Pilfering
7. Covering Tracks
8. Creating "Back Doors"
9. Denial of Service
1. FootPrinting:
Here a hacker would try and get the maximum information possible about the server/company/user. It includes details on IP addressing using the ARIN Whois, DNS transfers, etc. A hacker generally uses search engines, or the online whois database to find information they need.
2. Scanning:
Once you have the information you need about the target, the second stage involves target assessment and the identification of listening services. This includes scanning for open ports, trying to determine the OS being deployed, etc. The tools used in this stage include nmap, WS pingPro, siphon, fscan and mainly other popular utilities.
3. Enumeration:
The third stage includes identifying poorly protected resources, or user accounts that can be used to break into the network. This is where the default passwords and/or sample scripts are used to break into the network. Many network administrators who don't turn off the default guest account in Windows NT have let many hackers in. Or many services that are running by default e.g. the Network Printing services are easy targets for compromising security or latest exploits in the vendor software are easily picking.
4. Gaining Access:
Here the hacker's attempts to access the network with the information gathered in the previous three stages. The methods could be using buffer overflows, password file grabbing or even brute forcing the password. Tools like NAT, podium, or Lopht are commonly used.
5. Escalating Privileges:
If for example, the hacker gained access to just the guest account, now they would try to gain account of whole system. They would try to crack the password of administrators, or use exploits to increase the level of access. John the Riper an excellent password cracker is mostly used here.
6. Pilfering:
Again the information search begins to identify methods of gaining access to other systems and networks. Clear Text passwords (password saved as .txt files), or other not so safe mechanism for storing passwords are a boon to hackers. They can even search the registry for passwords.
7. Covering Tracks:
Once they have the information they need from the computer, hackers cover their tracks. They do this by clearing the system log files on the OS so that the system administrator cannot find out.
8. Creating "Back Doors":
Hackers leave backdoors in system, so next time they don't have to work this hard to gain entry. This could mean leaving Trojans disguised as valid application files, or new user accounts (where companies have 1000s of users). The tools they used are BO2K, keystroke loggers, or changing the registry keys.
9. Denial of Service (aka DoS):
Many crackers if unsuccessful use a DOS attack as a last mean of breaking into a system. If the system is improperly configured, it breaks down and lets the hacker into the system. The tools here used mostly are Pong Of Death, teardrop, and super nuker.
How to Protect Yourself?
You the end user, would ask how can I protect myself from all this? Simply stated, you can't. Nothing in this world is 100 percent safe. New exploits come out all the time. New methods are invented overnight. Things thought safe before, end up having weakness.
But here are a few guidelines to protecting yourself:
1. Install a good firewall and make sure it's configured properly.
2. Disable all system utilities not in use or services, which you don't use.
3. Never run any files sent to you from a total stranger.
4. Make sure you have good antivirus software installed and make sure you update the software on regular basis.
5. Make sure you have latest service pack and patches installed and subscribe yourself to one of the online security lists like SANS (System Administration, Networking and Security) network, which posts regular information on the latest exploits and the patches for the systems.
6. Have a good internal security policy.
7. Make sure you have a good network architecture designed to minimize risks.
8. Invest in good security hardware.
These are not the bible of security. These are just the common tips, which most people don't follow at their own risks. They cannot prevent hacks but can minimize it to a greater degree.
Security is not a joke or to be taken lightly. Without security, that dependence on computers can leave us wrecked virtually overnight. With the tools used by the cracker community being what they are, this is not just a proclamation. It's an Omen of what can be.
taken from TechiWarehouse
Saturday, June 23, 2007
How To Be A Better Blogger
feel free to e-mail me if anyone know who..
his/her writing..
I am already starting to learn some lessons about blogging. There is no doubt that I have a long way to go and lots to learn yet but I wanted to keep track of these blogging “rules” that I have discovered.
This is going to be a dynamic document that will change as often as I learn something new. You may want to keep an eye on this article in the future.
Keep Content Current
It is very important that you update your blog regularly and provide your visitors with reasons to return. If I go to a blog and see that the last entry was made six months ago (or six years ago), I am less likely to return to that blog than if the information is updated a few times a week.
You Will (Probably) Not Get Rich Blogging
There are literally millions of people who are willing to tell you how to make money blogging. But the truth of the matter is that a very small minority of people make a living blogging. If you are blogging only for the money, you would probably do better with a tin cup on a busy street corner. As an example, I am averaging about $0.33 per day with my blog. Do it because you are passionate about what you are blogging.
Now, with that being said, I’ve only been doing this for a short period of time and my blog isn’t terribly popular . It is entirely possible that I’ve got this completely wrong and everyone out there is getting rich.
Limit Your Advertisements
This goes along with what I wrote about above. Plastering your ads on every square inch of each web page only creates ad blindness. People just become “immune” to them. A couple of well placed ads do not take away from your website and add to your credibility.
Contribute to the Blogosphere
Take some time to visit other blogs of interest and write comments to their posts. When appropriate, mention different things that you have written about that pertain to the blog entry you are are commenting on. Even feel free to leave the web URI.When you contribute in this way, both the commenter and the author win.
Don’t Create “Spam” Comments
Don’t start going to every blog that you can find and posting something like:
Cool website! Check out mine! http://www.urblogadress.com
That’s a very good way to get yourself labelled as a spammer
Use Your Blogroll
If you find a good blog, add it to your blogroll and then e-mail the owner of the blog that you have done so. Often, they will reciprocate by adding you to their blogroll. This can do all kinds of wonders for you on Technorati and other such websites.
The other benefit to this is that you often gain new followers yourself in these bloggers. And if they like what they are reading, they will often write about you, sending even more traffic your way.
Respond to Your Comments
Comments are your reader’s way of intereacting with your writing. Thus, when they chose to add their two cents worth, it is common courtesy to reply.
Register with Search Engines
Make sure that people can find you and one of the best ways to do that is by registering with search engines. This way, when people look for you, they can find you.
Now, I know that there is a whole industry around search engine optimization (SEO) but there are two things that you can do that will help the most.
- Have a site map
- Use your keyword metatags
This will allow web bots to find you easier and categorize your pages better.
One little trick I learned early on was to sign up for some of the different webmaster tools that are provided by some of the search engines. For example, Google Analytics and Google Webmaster Tools keep you “in the face” of Google by having them perform tasks for you on a regular basis. This way, you can ensure that your content is being reviewed regularly. In fact, you can submit your site map right to Google so they can monitor it and then crawl your website.
Submit Your Pages To Social Bookmarking Sites
There are dozens of them out there. Two of the best ones that I have found are Digg and Reddit. Whenever I add a link to either of these sites, my hits jump immediately. And, I continue to see hits from them even after the initial surge.
Write About What You Know
I have heard about some people writing a “targetted” blog aimed to get traffic from a certain demographic. In my mind, this sounds like a bad idea about to get worse. Especially if you do not know what you are talking about. You could find your self alienated quite quickly and lose the blogging game before you even get started.
If you write about what you know, you will have better content, a more satisfying experience, and more respect from the blogging community.
Know Your Audience and Give Them What They Want
If you have a technical blog and most of the people who read it are looking for computer information, don’t suddenly start writing about flower arrangements. Keep on topic and you will keep your audience.
There is an exception. Regardless the blog, you can always pop in the occasional funny blog entry. Everyone likes to laugh now and again. Why not get that from your blog. If you can make it humor about your blog theme, even better!
This Is Just The Beginning
As I stated earlier, I am still very early in my blogging lifecycle. I plan to keep updating this page on a regular basis as I learn more useful things so check back from time to time. Hopefully we can continue to learn together.
Friday, June 22, 2007
worm breakout for Yahoo Messenger (YM)
This is how it look like
Use Firefox
Though there are some recently stir about the security vulnerabilities of Firefox, Mozilla made a patch for that in lightning Internet speed. Even better, the updates were sent to the browser when it is activated. I can go on and on telling you all the better security features of Firefox compared to IE (IE 7 is an exception). But you get the idea, don't compromise the safety of your PC, use Firefox. If you don't already have one, get it here : Get Firefox. If you already have and are using Firefox, then hooray for you
Use IM in a Virtual Environment
This is at the moment, my best suggestion. It may require a little extra effort for you to activate the IM in a virtual environment, but i really believe it is better to be safe than sorry. Using IM within a virtual environment decreases your percentage of getting worms like this one into your system ,down to nothing. Any worms that tries to infect your PC will be stuck in the virtual folder. If you would like to learn more about Virtualization, read this : Read Virtualization Article.
Ask
Ask your friend whether the link is legitimate, just make sure it was a human that sent you the link, not a bot. Sounds a bit silly for some people to do this, but there is not harm from asking, there is a lot of harm that follows a worm though, if it infects your PC
You may read the full report of the worm attack here : Read Full Report
You may also refer to Symantec.com for technical detail of the worm variant
at
6:56 PM
![]() .....
lAN
.....
lAN
Labels: internet, security, Yahoo Messenger
Saturday, June 16, 2007
Port Foward-Speed up your download
There are a couple of concepts you need to know before you can understand port forwarding.
1.) Every device on the internet has at least one ip address. The IP address is a number that is used to identify a device.
2.) Every IP address is divided up into many ports. When one computer sends data to another computer, it sends it from a port on an ip address to a port on an ip address.
3.) A port can only be used by one program at a time.
Now that we've got those general concepts out of the way let's talk about NAT. NAT is an acronym for Network Address Translation. NAT takes one ip address and basically breaks it into many ip addresses.
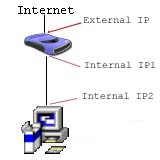
Here the external ip address is broken into two internal ip addresses. The first ip address "IP Address1" is the gateway. While "IP Address2" is the ip address of the first computer. Take note that the router has two ip addresses. It has the external ip address, and an internal ip address which acts as the gateway for every computer on the network.
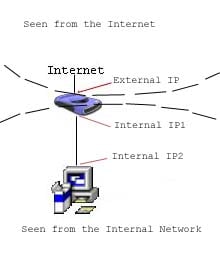
Computers on the internal network can only "see" internal ip addresses. So computers on the internal network can not send data directly to a computer outside of the network. When a computer on the network wants to send data to a computer outside of the network, it sends the data to the gateway. Remember the gateway is the internal ip address of the router. The router then takes this data and sends it out to the computer on the internet. The router sends the data out of the external ip address. The same thing is true of computers on the internet. A computer outside of the network can not "see" a computer inside of the network. They can only "see" and send data to the external ip address of the router. The router must then decide what to do with this data. Lucky for us NAT takes care of most of the work for us. There are some programs that NAT was not designed to work with, those are the programs we need to set up port forwarding for. Okay take a deep breath! We are on to port forwarding.
Now that you understand the general concepts of a network, explaining port forwarding is easy. When a computer on the internet sends data to the external ip address of the router, the router needs to know what to do with the data. Port Forwarding simply tells the router which computer on the local area network to send the data to. When you have port forwarding rules set up, your router takes the data off of the external ip address:port number and sends that data to an internal ip address:port number. Port Forwarding rules are created per port. So a rule set up for port 53 will only work for port 53.
A port can only be used by one program at a time! Think of how this rule interacts with NAT. Well you've only got one external ip address on your router. When computer 1 is using port 500, it is using port 500 on it's internal ip address. If you have set up a port forwarding rule for computer 1 and port 500, the external ip address's port 500 is also in use. This means that you can only use port 500 on one computer on the network at a time. Using port 500 on two computers at the same time would violate the one program rule, and your data would get messed up. Most routers require you to specify an internal ip address to forward ports to, just for this reason. Some do not, so be aware of this. Port Forwarding rules will only work for one computer at a time!....do portfoward now.
wow...The Coffee-Table PC!!
Nice gadget just release by Microsoft..
Microsoft has been looking beyond the desktop for sometime now, but with the launch of "Milan," the company is showing the potential for so-called "surface computing" to revolutionize everything from retail kiosks to the common coffee table. At its core, Milan is a PC running Windows Vista, but don't expect to use it with a keyboard and mouse. Instead, Milan uses a touch-sensitive display that enables multiple users to navigate the system's interface. See how it works!
Milan will start appearing in commercial locations at the end of this year (think casinos), but PC Magazine was able to sit down with Microsoft executives for a hands-on demo of the new system. The demo unit we saw looked a lot like a coffee table, but you won't want to put your feet up on this system; it was made for touching..read more











